Beware of PayPal phishing scam
Published February 07, 2025
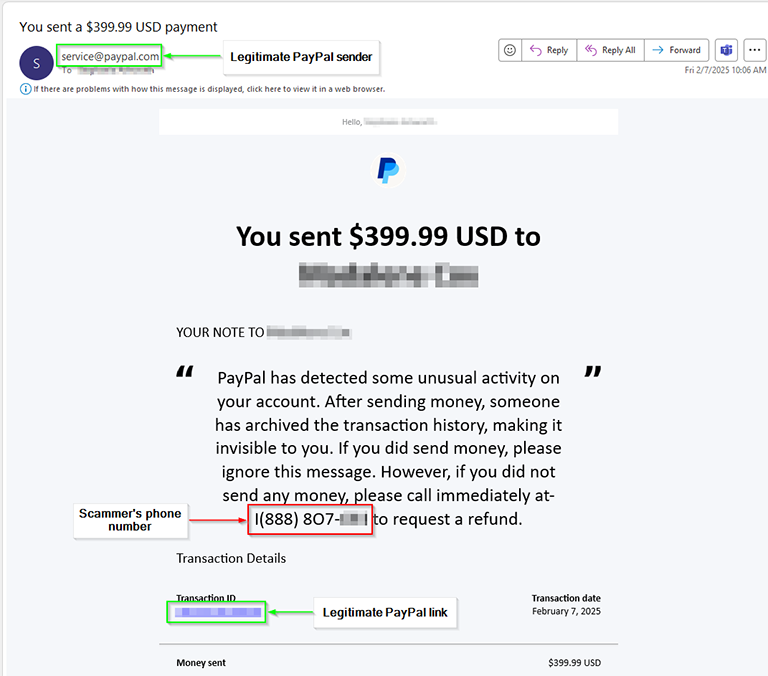
One of our team members received a scam email from the legitimate support@paypal.com email address today. In addition to the sender being a legitimate PayPal address, valid links to PayPal were also included in the email. So, where does the scam aspect come into play? Within the note there is a message (from the scammer) declaring that "PayPal has detected some unusual activity..." and the note goes on to list a phone number to call. This is NOT a valid phone number associated with PayPal. In…Read more
Don’t Tape Passwords to Your Computer
Published January 28, 2024

In the digital age, where cybersecurity threats are ever present, safeguarding our personal information is more critical than ever. Yet, some individuals still resort to outdated and risky practices, such as taping passwords to their computers. In this blog post, we'll explore the reasons why this seemingly convenient solution is a terrible idea and why you should opt for more secure password management practices. Risk of Unauthorized Access: Taping passwords to your computer exposes you to the…Read more
The power of password managers
Published December 05, 2023

Are you dominated by digital interactions and countless online accounts? Implementing and maintaining quality security measures has never been more critical. Protecting sensitive personal information from cyber threats is a priority for individuals and businesses alike. Among the most fundamental elements of safeguarding online data is the use of strong, unique passwords for every account. However, the task of managing numerous complex passwords is overwhelming. This is where password managers…Read more
Feeling Phishy: How to Be Safer in the Digital Ocean
Published November 06, 2023
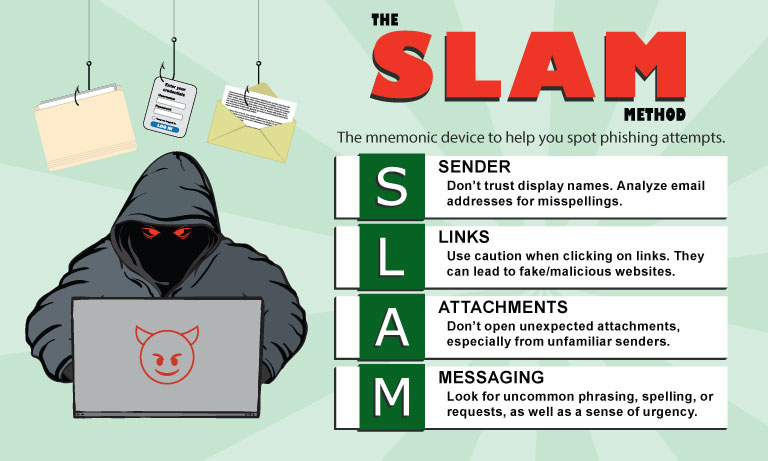
In today's digitally connected world, communication has never been easier, but alongside the convenience comes a pervasive threat—phishing emails. These deceptive messages lurk in our inboxes, masquerading as legitimate correspondence while aiming to deceive recipients. From individuals to large corporations, everyone is a potential target in the expansive net of cybercrime. Understanding the insidious nature of phishing emails and learning how to identify and combat them is crucial to…Read more
Where do cyberattacks start?
Published September 07, 2023

Have you ever wondered, "Where do cyberattacks start?" Well let me tell you, cyberattacks can happen on any device at any given time. Now you are probably wondering which devices should I protect and how. So, to understand this, it will help to understand where these attacks come from. In the past, most attacks came from outside sources, or, in other words, via the internet. IT Companies and cybersecurity specialists combatted these attacks by putting up firewalls, IDS, and IPS…Read more
Search Posts
Recent posts
Categories
Archives
- February, 2025 (1)
- January, 2024 (1)
- December, 2023 (1)
- November, 2023 (1)
- September, 2023 (1)
- July, 2023 (1)
- May, 2023 (1)
- April, 2023 (1)
- March, 2023 (1)
- January, 2023 (1)
- December, 2022 (1)
- November, 2022 (1)
- February, 2021 (1)
- March, 2018 (1)
- February, 2018 (1)
- October, 2017 (1)
- June, 2017 (1)
- April, 2017 (1)
- April, 2016 (1)
- February, 2016 (1)
- October, 2015 (1)
- July, 2015 (1)
- March, 2015 (2)
- February, 2015 (1)

