Exploits blog posts
NRC October 2024 Cybersecurity Summit
Published December 30, 2024

Panelist discussion at New River Computing's October 2024 Cybersecurity Summit New River Computing recently hosted a Cybersecurity Summit panel discussion on cybersecurity, cyber liability, and risk mitigation. The panel featured the following contributors: Jeff Wynn - IT Consultant and former president of New River Computing; Natalie Suarez - Principal Solutions Advisor, ConnectWise; Suzanne… Read more
Solarwinds, security, New River Computing, and you
Published February 05, 2021
Many recent news reports have come out regarding a massive hack of the Solarwinds Orion IT asset management system. This compromise is unprecedented in scale and reach, and the fallout from it will reverberate throughout the IT industry for years. Solarwinds Orion is one of many IT asset management systems (New River Computing uses one called Connectwise Automate). This software is great for… Read more
The cost of "free" software
Published April 11, 2016
Have you ever been tempted to try to acquire expensive software without paying for it? It turns out that "free" software can be more expensive than one might think! Take Photoshop for example: Subscribers can sign up and start using Photoshop for as little as $10, a far cry from the high upfront cost that it used to be, in the range of $600+. Adobe’s move to this subscription model… Read more
Top 5 risks of outdated technology
Published February 16, 2016
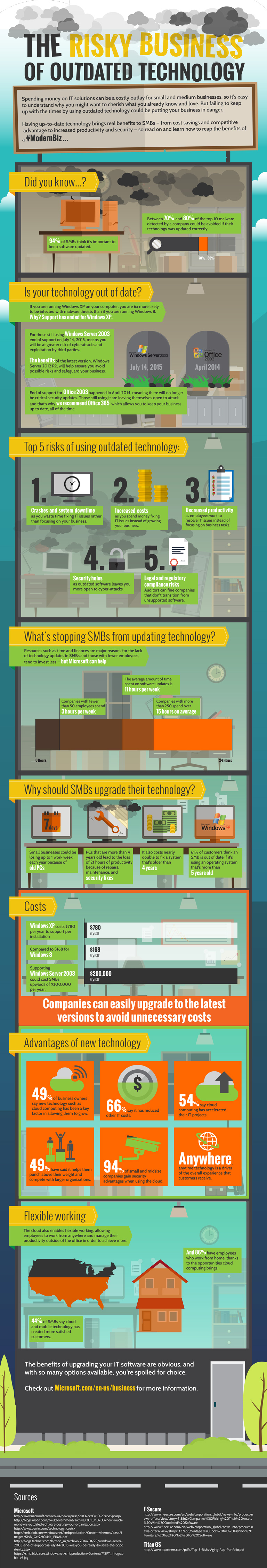
Click on the image below to view Microsoft’s infographic of The Risky Business of Outdated Technology! We can help - contact us for a free network review. Read more
The dangers of peer-to-peer-file sharing
Published April 25, 2014
Peer-to-Peer or P2P is a method of sharing of files between two or more computers on the Internet. Users share files via P2P by using peer-to-peer applications such as Gnutella, KaZaA, iMesh, LimeWire, Morpheus, SwapNut, WinMX, AudioGalaxy, Blubster, eDonkey, BearShare etc., and list goes on and on. How P2P Works The P2P application takes a piece of allotted data or sometimes whole directories… Read more
Search Posts
Recent posts
Categories
Archives
- February, 2025 (1)
- December, 2024 (1)
- January, 2024 (1)
- December, 2023 (1)
- November, 2023 (1)
- September, 2023 (1)
- July, 2023 (1)
- May, 2023 (1)
- April, 2023 (1)
- March, 2023 (1)
- January, 2023 (1)
- December, 2022 (1)
- November, 2022 (1)
- February, 2021 (1)
- March, 2018 (1)
- February, 2018 (1)
- October, 2017 (1)
- June, 2017 (1)
- April, 2017 (1)
- April, 2016 (1)
- February, 2016 (1)
- October, 2015 (1)
- July, 2015 (1)
- March, 2015 (2)

