Technology trends blog posts
Security and cyber liability panel discussion
Published January 20, 2023
New River Computing recently hosted a panel discussion on security and cyber liability featuring the following panelists: Jeff Wynn - President, New River Computing Jessica Swann - Cyber, Professional and Liability Broker, Risk Placement Services, Inc. Natalie Suarez - Principal Solutions Advisor, ConnectWise The panel was moderated by Jeff Nosenzo - Vice President of Brown Insurance. If you missed out on the panel or want to revisit it, you can check it out in the video above!Read more
The cost of "free" software
Published April 11, 2016
Have you ever been tempted to try to acquire expensive software without paying for it? It turns out that "free" software can be more expensive than one might think! Take Photoshop for example: Subscribers can sign up and start using Photoshop for as little as $10, a far cry from the high upfront cost that it used to be, in the range of $600+. Adobe’s move to this subscription model makes it easy for aspiring artists or even amateur photographers to use the professional software at a…Read more
Top 5 risks of outdated technology
Published February 16, 2016
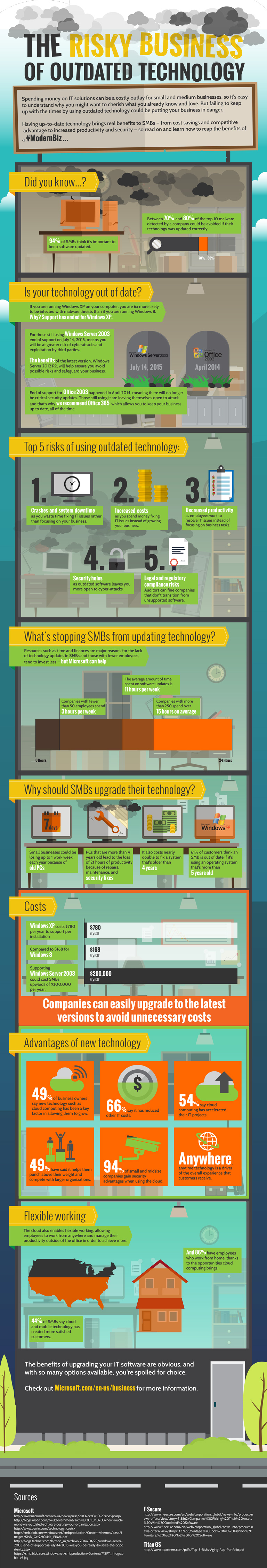
Click on the image below to view Microsoft’s infographic of The Risky Business of Outdated Technology! We can help - contact us for a free network review.Read more
HIPAA security – keeping data secure
Published July 24, 2015
If you are a "covered entity" under the HIPAA Security rule, then you already know that your company (and thus your employees) collect a lot of protected health information (aka PHI). PHI is basically information about another person that is not for public knowledge but needed in order to conduct business. What business? Information that insurance companies need to process claims and health care professionals need for continuity of care. Due to more recent mandates, healthcare entities…Read more
How will users upgrade to Windows 10?
Published March 18, 2015

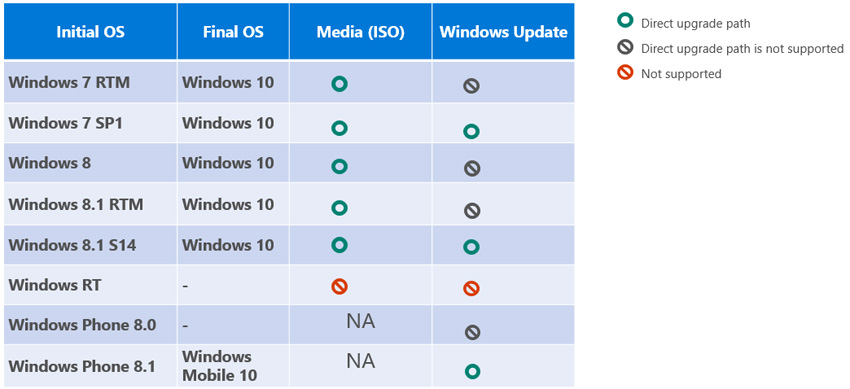
Microsoft seems to be (mostly) following Apple’s OSX strategy by making its own upcoming OS “Windows 10” a free upgrade. According to Thurrott.com, “Microsoft says it will deliver the final version of Windows 10 to 190 countries sometime between June 21 and September 23, 2015.” The update will be available to existing Windows 7, Windows 8.1 and Windows Phone 8.1 customers. Here is how users will be able to get this free upgrade: More information from Microsoft regarding Windows 10 can…Read more
Search Posts
Recent posts
Categories
Archives
- February, 2025 (1)
- January, 2024 (1)
- December, 2023 (1)
- November, 2023 (1)
- September, 2023 (1)
- July, 2023 (1)
- May, 2023 (1)
- April, 2023 (1)
- March, 2023 (1)
- January, 2023 (1)
- December, 2022 (1)
- November, 2022 (1)
- February, 2021 (1)
- March, 2018 (1)
- February, 2018 (1)
- October, 2017 (1)
- June, 2017 (1)
- April, 2017 (1)
- April, 2016 (1)
- February, 2016 (1)
- October, 2015 (1)
- July, 2015 (1)
- March, 2015 (2)
- February, 2015 (1)

