IT consulting and tech support blog
ZeroAccess Botnet
Published October 13, 2012
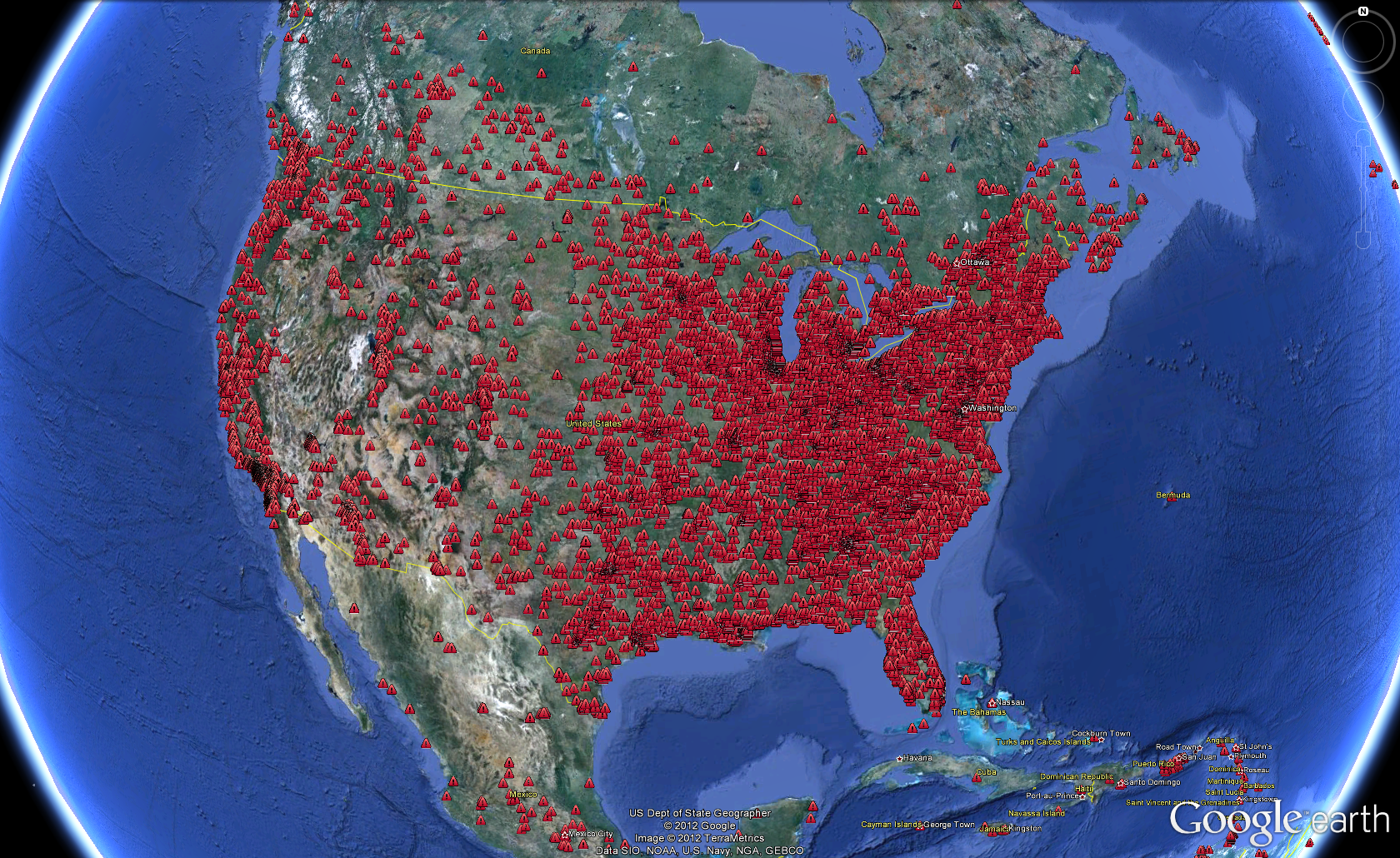
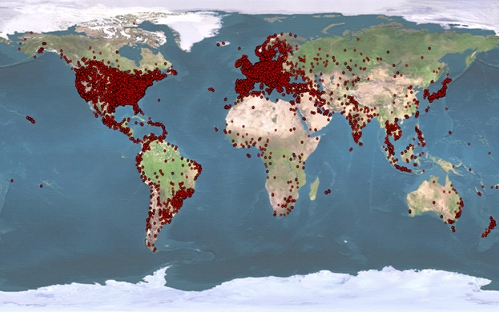
ZeroAccess is a very large botnet, infecting millions of computers globally. According to researchers at Sophos Labs, ZeroAccess has been installed on computers over nine million times with the current number of infected PC’s topping out at over 1 million. That is a staggering number. Below are some images that will give you a visual sense of just how widespread the infection is, not only in the… Read more
IE Zero-Day Fixit Tool available
Published September 20, 2012

Yesterday, Microsoft announced that it would be issuing an out-of-band patch on Friday, in response to the latest zero-day Internet Explorer vulnerability discovered this past weekend. For those users concerned about waiting, Microsoft released a FixIt tool on Wednesday that will temporarily neutralize the threat. Microsoft “FixIt” tools, are automated solutions that can diagnoses and… Read more
New IE Zero-Day vulnerability discovered.
Published September 18, 2012

Security researcher Eric Romang has discovered a new zero-day vulnerability in Internet Explorer, which he claims will affect fully patched versions of Microsoft Internet Explorer 7, 8 and 9. The exploits, developed over the weekend for the Metasploit exploit toolkit, have been linked to Nitro, the same group of hackers from China who were exploiting two Java zero-days in late August. “Since… Read more
SPAM!!!
Published September 10, 2012
A funny video about one of the most annoying things ever…SPAM!!! Read more
Disable Java…NOW!!!
Published September 04, 2012

Unfortunately, it appears that Java is once again unsafe. Over the weekend, the good folks over at security firm FireEye spotted a new attack that exploits a vulnerability in Java to install a Trojan named Poison Ivy, which communicates with C&C servers in China and Singapore. Since there’s no fix in sight, it is highly recommended that users turn off/disable Java in their browsers.… Read more
Search Posts
Recent posts
Categories
Archives
- February, 2025 (1)
- December, 2024 (1)
- January, 2024 (1)
- December, 2023 (1)
- November, 2023 (1)
- September, 2023 (1)
- July, 2023 (1)
- May, 2023 (1)
- April, 2023 (1)
- March, 2023 (1)
- January, 2023 (1)
- December, 2022 (1)
- November, 2022 (1)
- February, 2021 (1)
- March, 2018 (1)
- February, 2018 (1)
- October, 2017 (1)
- June, 2017 (1)
- April, 2017 (1)
- April, 2016 (1)
- February, 2016 (1)
- October, 2015 (1)
- July, 2015 (1)
- March, 2015 (2)

