Cybersecurity blog posts
‘Microsoft tech support’ scam captured on video
Published April 11, 2013
For those of us working in the IT industry, we get used to removing viruses and malware from plenty of machines on a regular basis. Malware is a huge problem that seems to only be getting worse. Part of the problem is a lack of education for the end users. It’s easy for the less tech savvy to get tricked into downloading a piece of software that disguises itself as legitimate piece of software… Read more
Ransomware attacks appear to be getting worse
Published January 22, 2013




For those of you not familiar with exactly what Ransomware is/does, here’s the current Wikipedia definition: “Ransomware comprises a class of malware which restricts access to the computer system that it infects, and demands a ransom paid to the creator of the malware in order for the restriction to be removed. Some forms of Ransomware encrypt files on the system’s hard drive, while some may… Read more
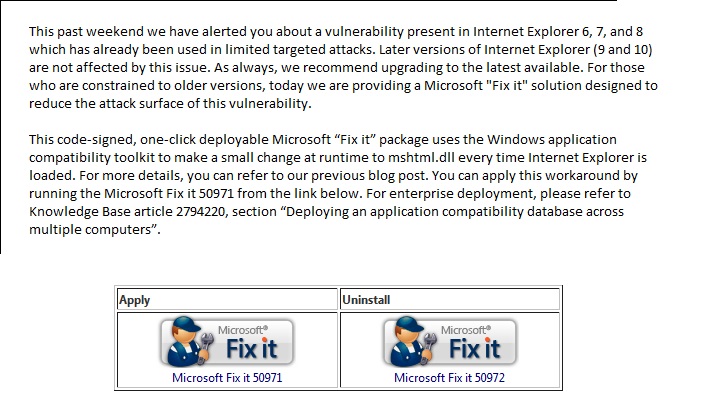
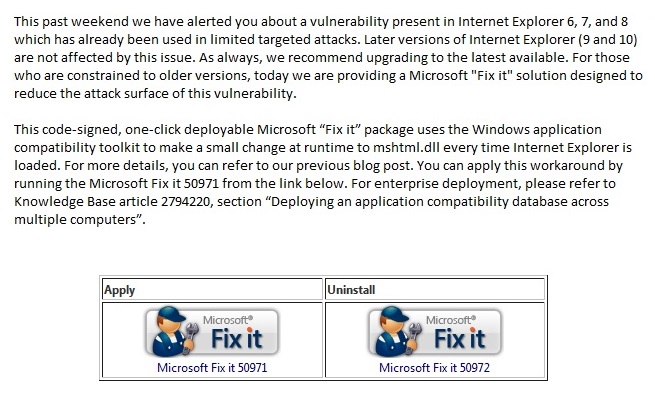
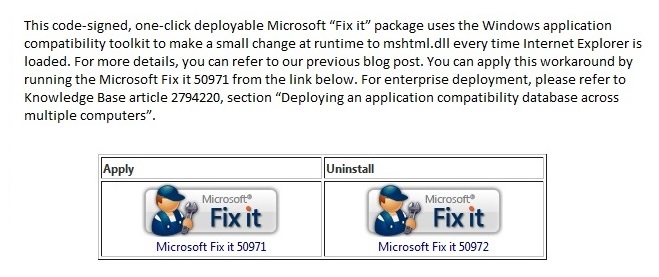
Internet Explorer 8 Zero-Day Vulnerability
Published January 07, 2013

**ATTENTION**: If you are a current New River Computing client covered under our RMM Service Plan, you need not worry about this vulnerability. We have automatically deployed the fix to your computers. Recently, there has been an Internet Explorer (zero-day) remote code execution vulnerability found being exploited in the wild which affects IE 8, as well as IE 6 & 7. Current exploitation is… Read more
Can you tell the difference between real vs. rogue security software?
Published January 07, 2013


Rogue security software, also known as fake antivirus software or “scareware”, has been one of the most popular methods used by online criminals in recent years to fool computer users into installing malware and/or divulge confidential information. Rogue AV software typically mimics the general look and feel of legitimate security software programs. Once installed on a person’s… Read more
Nationwide Insurance breach puts over 1 million customers at risk
Published December 18, 2012

Over 1 million customers are at risk of identity theft after online-criminals broke into servers belonging to Nationwide and Allied insurance companies. Victims include current policyholders and those who sought insurance quotes. The breach took place Oct. 3 and was discovered the same day. Nationwide immediately contacted authorities, but waited to inform their customers directly. “Although we… Read more
Search Posts
Recent posts
Categories
Archives
- February, 2025 (1)
- December, 2024 (1)
- January, 2024 (1)
- December, 2023 (1)
- November, 2023 (1)
- September, 2023 (1)
- July, 2023 (1)
- May, 2023 (1)
- April, 2023 (1)
- March, 2023 (1)
- January, 2023 (1)
- December, 2022 (1)
- November, 2022 (1)
- February, 2021 (1)
- March, 2018 (1)
- February, 2018 (1)
- October, 2017 (1)
- June, 2017 (1)
- April, 2017 (1)
- April, 2016 (1)
- February, 2016 (1)
- October, 2015 (1)
- July, 2015 (1)
- March, 2015 (2)

