Cybersecurity blog posts
How cyber-criminals steal money from bank accounts.
Published December 17, 2012

Here’s a great info-graphic from the security researchers at F-Secure that explains how cyber-criminals steal money from bank accounts. The original post can be found here. Read more
Microsoft Security Essentials fails to meet AV-TEST standards
Published December 02, 2012

Researchers at the independent anti-virus testing firm AV-TEST released their latest batch of tests in which they report Microsoft Security Essentials was only able to detect 64% of zero-day threats when running in Windows 7. Due to the pitifully low score, MSE failed to receive the AV-TEST Institute’s seal of approval, a certification granted to products that meet 11 of 18 assessment criteria.… Read more
Tips to help keep your computer safe online
Published October 22, 2012
Unfortunately, the Internet is not a very safe place. Online threats and scams are never too far away. With today’s never-ending barrage of information in cyberspace, it can be difficult to stay on top of the fundamental security procedures that we all need to stick to. Many users fall victim to flashy Anti-virus advertising that promises to offer “Complete Security or Total Protection”… Read more
ZeroAccess Botnet
Published October 13, 2012
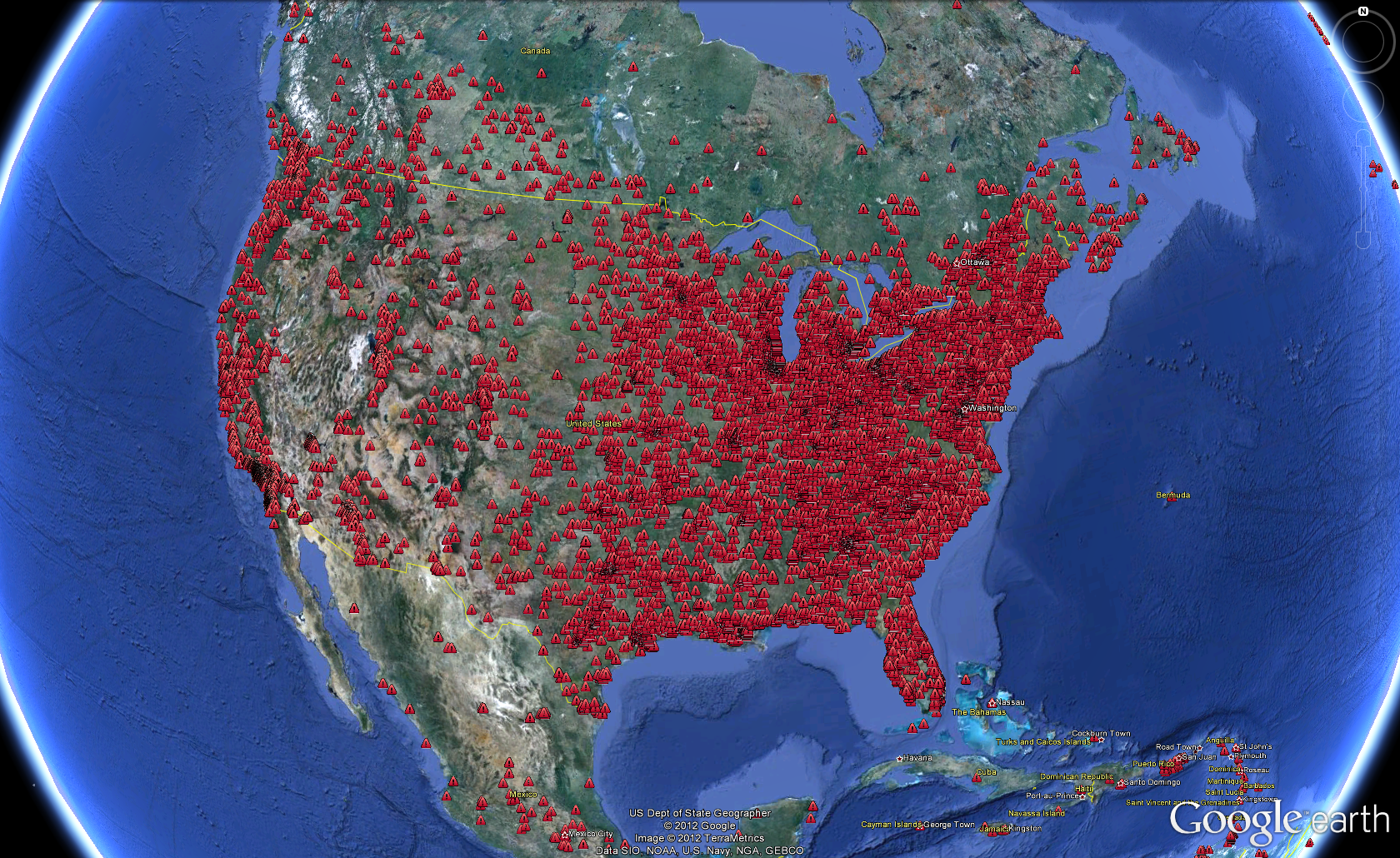
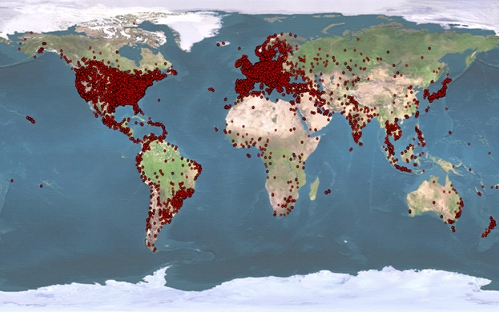
ZeroAccess is a very large botnet, infecting millions of computers globally. According to researchers at Sophos Labs, ZeroAccess has been installed on computers over nine million times with the current number of infected PC’s topping out at over 1 million. That is a staggering number. Below are some images that will give you a visual sense of just how widespread the infection is, not only in the… Read more
IE Zero-Day Fixit Tool available
Published September 20, 2012

Yesterday, Microsoft announced that it would be issuing an out-of-band patch on Friday, in response to the latest zero-day Internet Explorer vulnerability discovered this past weekend. For those users concerned about waiting, Microsoft released a FixIt tool on Wednesday that will temporarily neutralize the threat. Microsoft “FixIt” tools, are automated solutions that can diagnoses and… Read more
Search Posts
Recent posts
Categories
Archives
- February, 2025 (1)
- December, 2024 (1)
- January, 2024 (1)
- December, 2023 (1)
- November, 2023 (1)
- September, 2023 (1)
- July, 2023 (1)
- May, 2023 (1)
- April, 2023 (1)
- March, 2023 (1)
- January, 2023 (1)
- December, 2022 (1)
- November, 2022 (1)
- February, 2021 (1)
- March, 2018 (1)
- February, 2018 (1)
- October, 2017 (1)
- June, 2017 (1)
- April, 2017 (1)
- April, 2016 (1)
- February, 2016 (1)
- October, 2015 (1)
- July, 2015 (1)
- March, 2015 (2)

